Biometric authentication is rapidly becoming the foundation for how people pay, access secure spaces, and verify their identities across industries. However, as adoption grows, a critical question arises: How can a palm scanner, or any biometric system, verify that the presented identity is genuine and not a spoofed attempt?
At Keyo, we’ve spent years designing palm-based identity solutions that work not just in ideal conditions, but also in the real world: where fraud attempts, environmental challenges, and privacy requirements collide. Detecting fake identities isn’t optional; it’s a fundamental part of building trust in biometrics.
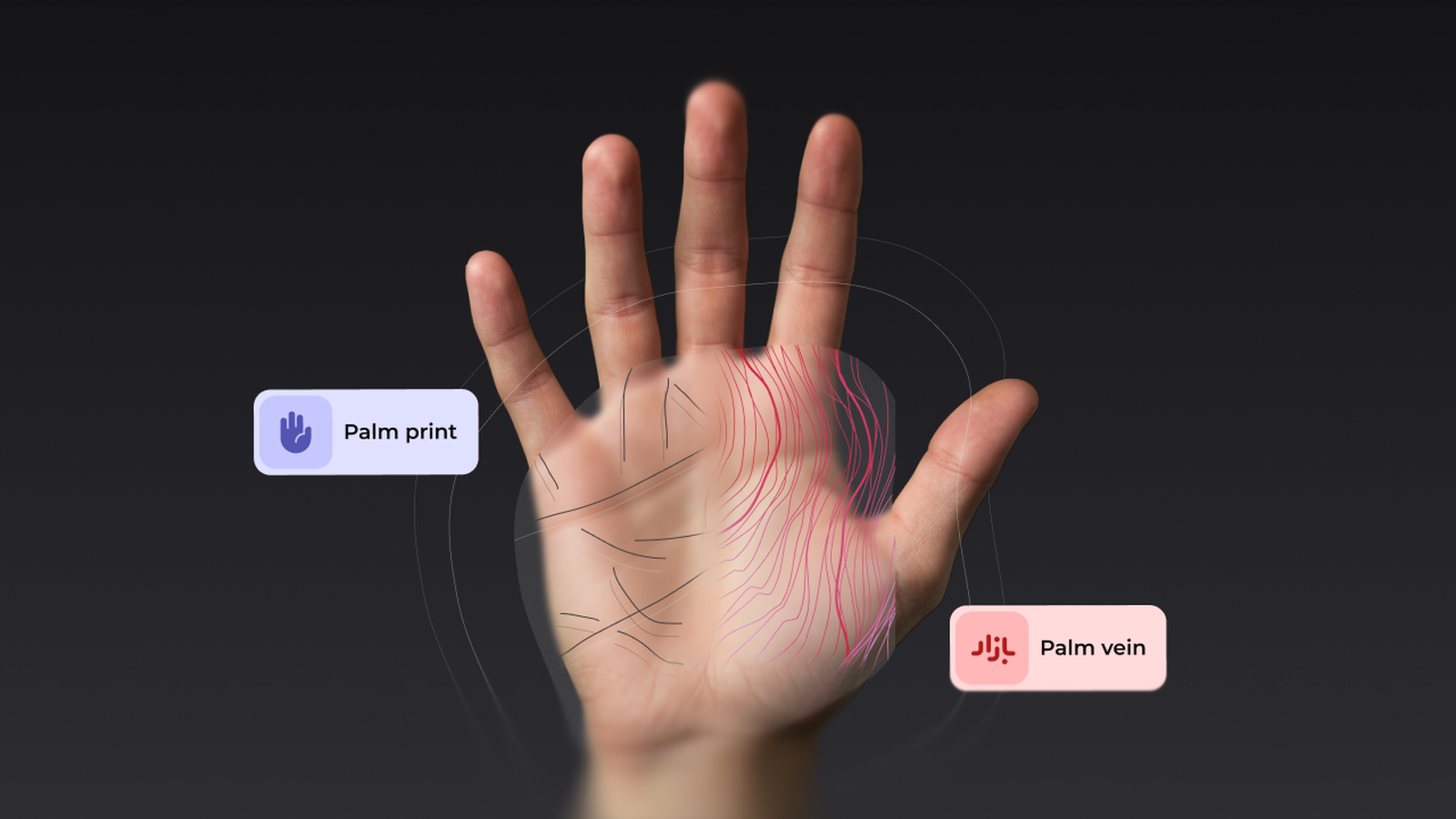
Palm recognition goes beneath the surface
Most people think of biometrics as something surface-level: a fingerprint, a face, or an iris. Palm recognition goes further. Keyo’s approach uses a dual-layer method that combines:
Palm print patterns: the ridges and textures on the surface of the hand.
Vein patterns: the unique, invisible network of veins beneath the skin, captured using near-infrared light.
This combination makes palm biometrics extremely hard to replicate. While a fingerprint can be lifted from a surface or a face can be photographed, vein patterns exist internally and can only be detected by specialized sensors. That means a palm scanner like Keyo’s isn’t just “looking” at your hand—it’s mapping a signature that is hidden inside your body.
Why liveness detection matters
Even the best biometric system can be vulnerable if it can’t distinguish between a living person and a fake object. That’s where liveness detection comes in.
Keyo palm scanners apply several liveness checks to make sure the system is interacting with a real human being:
Blood flow detection: Infrared light interacts with hemoglobin, allowing the scanner to confirm active circulation in the veins.
3D imaging: Palm scanners measure depth and shape, preventing fraudsters from using flat photos, prosthetics, or silicone molds.
Natural motion analysis: Keyo’s software can pick up on micro-movements of the hand during the scan, ensuring that the biometric is being presented live, in real time.
These combined signals allow palm systems to reject spoofing attempts, whether they involve a photograph, a fake hand model, or even advanced deepfake-style replicas.
Multi-factor matching: More than one signal
Biometric security is most effective when it doesn’t rely on a single trait. Keyo’s palm authentication combines multiple independent signals to create a highly reliable match:
Surface palm print data
Subdermal vein patterns
Liveness signals from circulation and motion
Together, this fusion of biometric markers makes the chance of spoofing incredibly small. It’s not enough to replicate one layer; you would need to mimic them all, simultaneously, in a way that satisfies the scanner’s detection thresholds. For would-be attackers, that’s not just difficult; it’s nearly impossible.
Privacy and security by design
Detecting fakes is only part of the equation. Businesses and regulators also demand that biometric systems respect user privacy and data security. Keyo’s platform is built on a privacy-by-design, zero-trust architecture that ensures:
Data sovereignty: User data stays in the region it was collected, in compliance with local regulations.
On-device processing: Palm images are converted into encrypted templates and matched directly on the device, so raw biometric data doesn’t travel across networks.
Encryption and minimization: Biometric templates are protected with strong encryption and designed so they can’t be reverse-engineered into a raw image of a person’s hand.
This approach enables businesses to integrate advanced biometric authentication while protecting users and meeting compliance standards without compromising on either.
Why spoof detection is critical for businesses
Whether in payments, healthcare, government, or transportation, the risk of identity fraud is high. A spoofed biometric doesn’t just lead to a single fraudulent transaction, it can undermine trust in the entire system.
By using palm biometrics with multi-layer spoof detection, organizations gain:
Fewer chargebacks and fraud losses in payments.
Cleaner authentication for access control, reducing false declines and manual checks.
Greater user confidence that their data and identity are secure.
Keyo’s palm platform brings these benefits into environments that are notoriously challenging: crowded retail stores, airports with mixed lighting, hospitals with masked patients, and financial institutions where fraud prevention is non-negotiable.
The Key takeaway
Palm scanners aren’t just checking for a match, they’re verifying that the identity presented is unique, alive, and genuine. By combining surface and subdermal data with liveness detection and strong privacy protections, solutions like Keyo make spoofing virtually impossible while keeping users’ identities safe.
In an era where fraud is getting more sophisticated, businesses need biometric tools that can stay one step ahead. Palm recognition, done right, provides exactly that.
Learn more at keyo.com or contact us hello@keyo.co
 Biometric Authentication: How it works & why palm leads
Biometric Authentication: How it works & why palm leads Biometric Wallets vs. Mobile Wallets: Why Palm Recognition Is the Future of Payments
Biometric Wallets vs. Mobile Wallets: Why Palm Recognition Is the Future of Payments